Encryption
Quantum Computers Will Break Current Encryption
Protects Long-Term Sensitive Data
Enables Unhackable Communications
Broader Societal & Economic Stakes
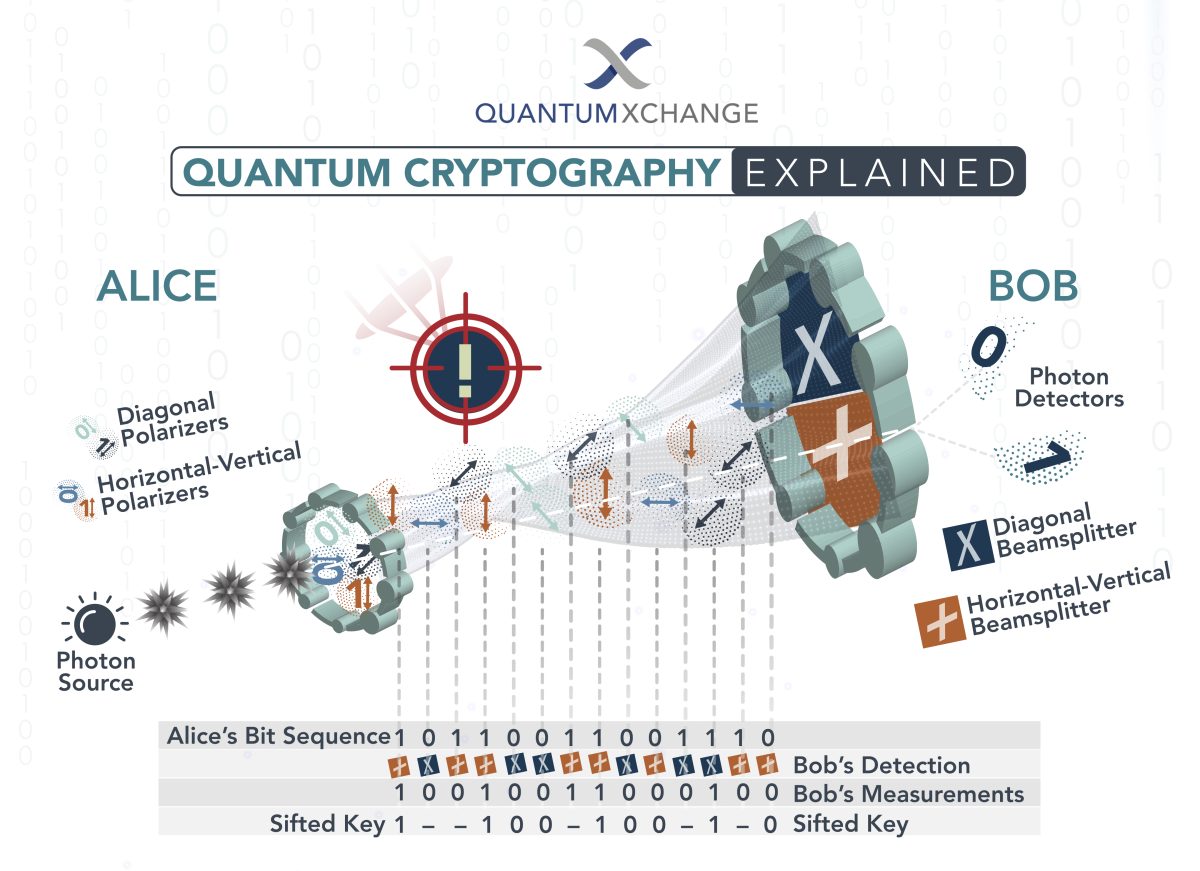
Today's systems (e.g., RSA, ECC) rely on "hard" math problems like factoring huge primes, which supercomputers can't solve efficiently (trillions of years needed). But quantum machines, using qubits in superposition, run Shor's algorithm to crack them in minutes. NIST predicts viable quantum threats in 10-20 years, and "harvest now, decrypt later" attacks are already underway—hackers steal encrypted data today for future quantum decryption.
Classical encryption secures data for ~10-30 years, but quantum-safe methods (like QKD) can lock it for 100+ years. Vital for healthcare (HIPAA-protected records), finance (blockchain ledgers), and governments (classified intel). In 2025, with 85%+ of physicians using electronic records, breaches could expose lifetimes of personal data.
QKD detects eavesdroppers in real-time via quantum disturbance—impossible to copy or spy without alerting parties (no-cloning theorem). This "information-theoretic security" is provably unbreakable, even by unlimited compute power. As cyber threats evolve (e.g., AI-driven ransomware hitting 66% of orgs in 2024), it future-proofs global infrastructure like 5G networks and cloud computing
Without it, cryptocurrencies collapse, supply chains halt (tampered IoT data), and nations face espionage windfalls. NIST's 2024 post-quantum standards (e.g., CRYSTALS-Kyber) show urgency—organizations must migrate now for "crypto-agility." In a quantum world, it's not about if breaches happen, but when—and quantum encryption ensures we're ready.
Secure Connection
You should always use HTTPS instead of HTTP to ensure secure and encrypted communication over the internet, protecting your sensitive information from being intercepted or tampered with by malicious actors.
User Agent
A user agent is a software agent responsible for retrieving and facilitating end-user interaction with web content. It is a string of text sent by a web browser to a web server to identify itself and provide information about the browser’s capabilities.
In today’s digital landscape, cybersecurity threats are becoming increasingly sophisticated, and hackers are constantly evolving their tactics to breach even the most secure systems. To effectively defend against these threats, it’s essential to understand the tools and methods hackers use to compromise systems. Kali Linux, a popular hacking operating system, provides a unique opportunity to learn about these tools and techniques. By familiarizing yourself with Kali Linux, you’ll gain a deeper understanding of the hacking mindset and the methods used to exploit vulnerabilities. This knowledge will enable you to anticipate and prepare for potential attacks, ultimately strengthening your organization’s defenses.
Capabilities of Hackers, Tools Hackers use, and 5 Things You Can Do To Protect Yourself
These are just a few of the tools that Ryan can effectively operate to penetrate various aspects of our daily lives, such as cars, locations with access codes, RFIDs, Wi-Fi, and more. Ryan also provides guidance on what we can do to protect ourselves against hackers. To learn more, watch the full segment on the Shawn Ryan Show.
Threat Landscape
When it comes to being hacked, there are many different attack vectors that attackers can use to gain access to your personal information or devices.
To protect yourself from being hacked, it is important to be vigilant and take steps to secure your personal information and devices. This includes using strong passwords, avoiding suspicious emails and websites, keeping your software up to date, and using security tools such as antivirus software.